Security Operation Centers have evolved from SIEM-based detection to threat hunting and SOAR automation, but AI-driven cyberattacks now threaten to overwhelm SOC analysts with higher alert volumes and rapidly unfolding threats. Attackers will soon be able to build ransomware or exploit vulnerabilities within minutes, forcing SOCs to transform again. Gruve focuses on two priorities: reducing analyst burnout through AI-optimized handovers and real-time technical support, and strengthening customer security by using AI to deepen analysts’ understanding of complex IT security domains. By embedding AI across tools and training, SOC analysts gain the capability to respond faster and improve overall security posture.

Discover the evolution of Security Operation Centers (SOCs) and how AI is transforming operations, boosting analyst efficiency, and strengthening customer security posture against increasingly sophisticated cyber threats.
AI SOC Transformation
Over the last 15 years, Security Operation Centers (SOCs) have gone through several transformations. Due to the developing nature of cyber-attacks, the technologies leveraged in SOCs have required modifications, upgrades, and adaptability to match these threats. Additionally, through this timeframe, the skillsets of the SOC Analyst have morphed.
Initially, SOCs utilized Security Information and Event Management (SIEM) platforms to detect, analyze, and respond to threats. Years later, SOCs adopted more proactive approaches, like threat hunting, and the use of threat intelligence feeds to anticipate and mitigate potential risks.
In the last several years, security automation and orchestration have become integral to SOCs. Security Orchestration, Automation, and Response (SOAR) platforms have become key technology for SOCs in streamlining repetitive tasks, enhancing response times, and automating workflows.
While these tools have played a significant role in helping the SOC Analyst improve their visibility into their customers’ security posture and help their customers defend against cyber threats, their responsibilities and expectations have amplified.
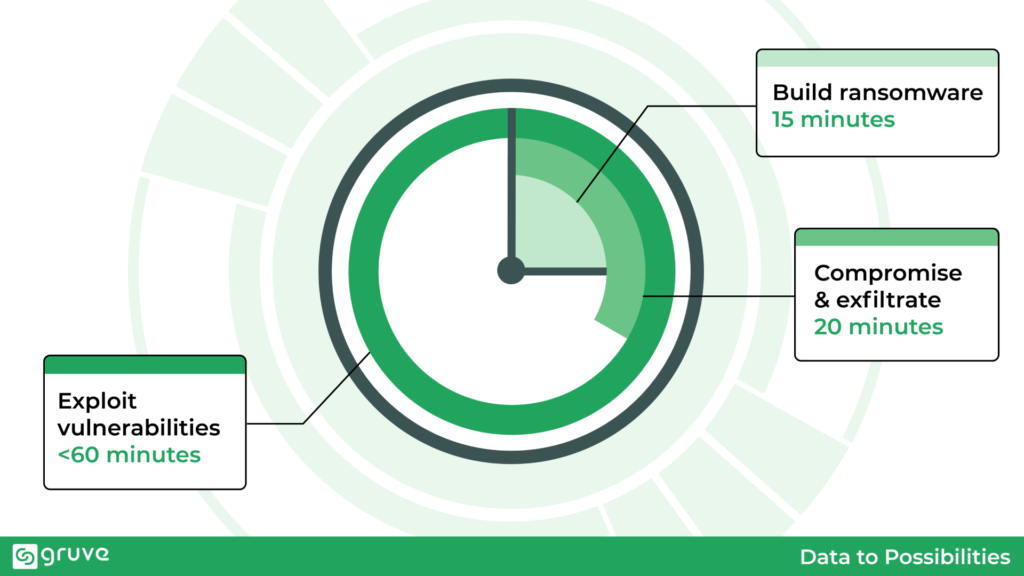
Recently, artificial intelligence (AI) has become the latest technology trend. Unfortunately, with the power of AI, malicious actors have been able to quicken the time to cause damage to organizations. It’s projected that by 2026 malicious actors will be able to accomplish the following:
- Build ransomware in 15 minutes
- Compromise and exfiltrate in 20 minutes
- Exploit vulnerabilities in less than 60 minutes
With cyber threats emerging and being deployed in under an hour, SOCs must transform once again. While this new phase takes form, the role of the SOC Analyst will face several challenges. There will be higher alert volumes and more complex attack vectors. Consequently, the work environment for the SOC Analyst may become more stressful.
At Gruve, with the aid of AI, the two of the biggest challenges for SOC Analysts that we are perpetually solving are the following:
- SOC Analyst Burnout
- Continuously Improving Customers’ Security Posture
SOC Analyst Burnout

The heart of the SOC are the SOC Analysts. However, the number of alerts, events, incidents, and tickets can quickly overwhelm even the most experienced SOC Analysts. With the rise of AI-powered attacks, the demands of an average workday are likely to become more intense and stressful for SOC Analysts. To address these challenges, we are actively exploring how AI can be utilized to create a more efficient and supportive work environment for our SOC Analysts.
Our first objective is to ensure that SOC analysts remain focused and are well rested. While a standard SOC shift is typically eight hours, analysts often arrive early or stay late due to the knowledge transfers that happen during shift handovers. This will worsen as AI cyber-attacks increase. To combat this, we’re investigating AI-driven cybersecurity solutions to optimize the handover process. By automating and streamlining these transitions, analysts can focus their full eight-hour shifts on their core responsibilities and enjoy uninterrupted personal time outside of work.
Additionally, we are looking to AI to help address another critical challenge: providing SOC analysts with the technical support they need. Especially for newcomers, whether to the industry or to an organization, it can be intimidating to seek advice from colleagues, often due to concerns of judgment or criticism. This can lead to tremendous stress when trying to solve problems individually. AI can help bridge this gap by creating a safe and inclusive forum where analysts can ask questions and access real-time guidance without fear or hesitation.
Continuously Improving Customers’ Security Posture
To continuously improve our customers’ security posture, we are harnessing AI to enhance our SOC Analysts’ understanding of the evolving IT security landscape. With hundreds of security products and solutions available today and dozens more emerging annually, it’s critical to understand not only how these tools function but also how they integrate. Also, it’s critical that the SOC Analyst understands the different types of logs that are generated from different IT Security areas.
The key areas of IT security we target include:
- User and Device Security
- SASE/Security Services Edge
- SDWAN
- Network Security
- Application Security
- Data Security
We aim to incorporate AI to educate and refine the skills of our SOC Analysts, enhancing their ability to understand IT security areas and how various solutions work together. By doing so, we can ensure they are prepared to advise customers not just on identifying alerts or threats but also on taking precise and actionable steps to mitigate risks.
Also, within the ecosystem of products and solutions powering our SOC, like SIEMs and SOARs, we are committed to ongoing research to enable and optimize AI features. This includes establishing thorough evaluation criteria to assess how these capabilities contribute benefits for both our SOC Analysts and our customers.
Our criteria for AI effectiveness include:
- Reduction of false positives to focus on real threats
- Improved prioritization of events for more efficient responses
- Increased usage and effectiveness for SOC Analysts ensuring AI tools deliver meaningful insights
AI Empowered SOC Analysts
In this new era of SOC Transformation, though AI will be the technology that nefariously helps create cyber-attacks, AI will be incorporated in every facet within our SOC where we see a positive impact. For our SOC, we will start this transformation with the primary focus on our SOC Analysts.
We want our SOC analysts to be prepared for the upcoming cybersecurity threats and we want our customers to be best protected. To accomplish this, we must empower our SOC Analysts with AI. We believe it’s our responsibility to foster an environment where our SOC Analyst can take advantage of AI and truly embrace all its benefits.
FAQ
What’s driving the next SOC transformation?
AI-accelerated attacks now unfold in under an hour (ransomware in ~15 min, exfil in ~20, exploits <60), creating higher alert volumes and complexity that traditional workflows can’t keep up with.
Will AI replace SOC analysts?
No, AI augments analysts. It automates busywork (handoffs, triage, enrichment) and provides real-time guidance so humans can focus on judgment, escalation, and customer impact.
How does AI reduce SOC analyst burnout?
By automating shift handovers, suppressing low-value noise, and acting as a safe “on-demand teammate” for questions and playbook help so analysts use their full shift on core work and actually disconnect off-shift.
How does AI improve customer security posture?
It deepens analysts’ understanding across domains (User/Device, SASE, SD-WAN, Network, App, Data), maps logs to risks, and recommends precise, actionable steps not just alerts.
How will Gruve measure AI effectiveness in the SOC?
Clear criteria: fewer false positives, better event prioritization, faster, more confident analyst actions, and sustained analyst adoption where AI delivers meaningful insights.